Importance of Cloud IAM (Identity and Access Management): The Current Outlook

Introduction
In today’s IT landscape, identity and access management (IAM) is an important topic. The importance of Cloud IAM has been well-established by many organizations, but there are still some misconceptions about how the technology works and what it can do for your organization.
According to a 2022 report by Gartner, leaders in the security and risk management space are faced with rapidly increasing disruptions in the identity and access management (IAM) space.
Cloud IAM solutions help mitigate the challenges by amplifying the aspect of security for remote workforces that have proliferated because of the pandemic and can effectively handle the customer-facing interactions on the digital channels. CIOs across the globe are increasingly considering integrating IAM infrastructure into their cloud architectures.
Identity and access management (IAM) is an essential part of cloud services. It allows you to control who has access to the resources you have purchased and who can manage these resources.
In a world full of cyberattacks and data breaches, IT managers can ensure the safety of their data by leveraging cloud-based security. With cloud-based security and identity management (IDM) solutions, organizations can take control of all activities related to the access and management of identities in the enterprise.
According to NTT Communications, over 50% of companies surveyed reported that more than half their cybersecurity budgets are spent on external threats — with “cloud-based data breaches” being a top threat category.
With cloud IAM one can grant access to cloud resources at different well-defined levels, well beyond the project-level access. Enterprises can create more granular access control policies for resources based on multiple attributes like device security status, IP address, resource type allocated, and date/time.
The following are some essential features of cloud IAM services:
a) Clean & Consistent Single Access Control Interface – Cloud IAM solutions provide a clean and consistent interface for all cloud platform services. The same interface can be used for all cloud services, regardless of which provider you’re using.
Access control for cloud services is a challenge.
In most cases, access control management is not a service that a developer platform provides. It’s often provided by an external provider, or it’s built into the platform but only supports a limited number of Cloud IAM solutions.
b) Optimized Security – Cloud IAM allows one to define increased security for critical applications.
One can also define increased security for all applications, or for only selected applications. As one can define increased security for critical applications, one can also control who is able to access your system and what they are able to do while they are on it. The number of people who have access to specific functions can be restrained, like creating new users or changing passwords.
In general, there are three ways for you to define increased security for critical applications:
– Virtual Network Security (VNS): This feature acts as an extra layer of protection, blocking unauthorized access to your network from anywhere on the internet.
– Encryption: We can use encryption to protect the information in transit and at rest.
– Multi-factor authentication (MFA): This feature allows users to log in using two different types of authentication methods at the same time.
c) Resource-Level Access Control: Resource-level Access Control is a way to define roles and grant permissions to users to access resources at different granularity levels.
For example, if you want to allow your most trusted friends access to your company’s internal network but not your customers’ data, you could create a role called “friend” that gives them access to the internal network while denying them access to the customer data. This would allow them easy access to the business information they need but keep their personal information secure.
RLAC allows one to define roles and grant permissions to users to access resources at different granularity levels. It’s useful for restricting access to resources based on their type, for example, restricting a user’s ability to edit files in their project folder.
According to Gartner by the year 2023, 40% of IAM application convergence will primarily be dictated via managed security providers (MSSPs) that will accelerate the competition for best-in-class solutions and an integrated approach.
As the focus will shift from product vendors to service partners, identity proofing tools will be implemented within the workforce identity life cycle and the increased adoption of cloud IAM solutions will gain antecedence.
In this article, we’ll discuss why cloud IAM is so important and what you should know about it before deciding whether or not it’s right for your organization.
The Importance of Cloud IAM
Cloud IAM is a set of tools that help manage the identity and access management for cloud resources. It’s important for cloud security, compliance, governance, and management.
Cloud IAM helps you secure your data by providing a centralized view of who has access to what information. This helps ensure that only authorized users can access sensitive data in your organization’s AWS account.
It also enables you to comply with regulations like GDPR (General Data Protection Regulation) or SOX (Sarbanes-Oxley Act) by enforcing employee consent requirements on any new hires entering an organization’s network environment – including mobile devices used by employees outside of work hours – which means fewer breaches due to inadvertent disclosure or accidental loss/misplacement of personal information when it shouldn’t have been shared in the first place!
Cloud IAM: The Current State of Affairs
Cloud IAM is important for many different reasons and is increasingly being adopted by enterprises globally. It can help security professionals to:
- Secure your organization’s cloud resources, whether by protecting endpoints or providing permissions in the case of SaaS applications and on-premises workloads.
- Ensure compliance with industry standards like PCI DSS and ISO 27001, as well as internal policies such as Sarbanes Oxley (SOX).
- Reduce costs by automating routine tasks associated with identity management so that other departments don’t have to spend time doing them manually. This means less pressure on security teams, which leads directly to greater productivity for all involved in protecting data assets at scale.
Cloud IAM is Important to Reframe Conventional Cybersecurity Models & Approaches
Cloud IAM is important because it is the backbone of any cloud application. The ability to manage identity and access control in a secure and scalable way will ensure that your users are able to access only those resources they need while keeping their information secure by preventing unauthorized access or modification.
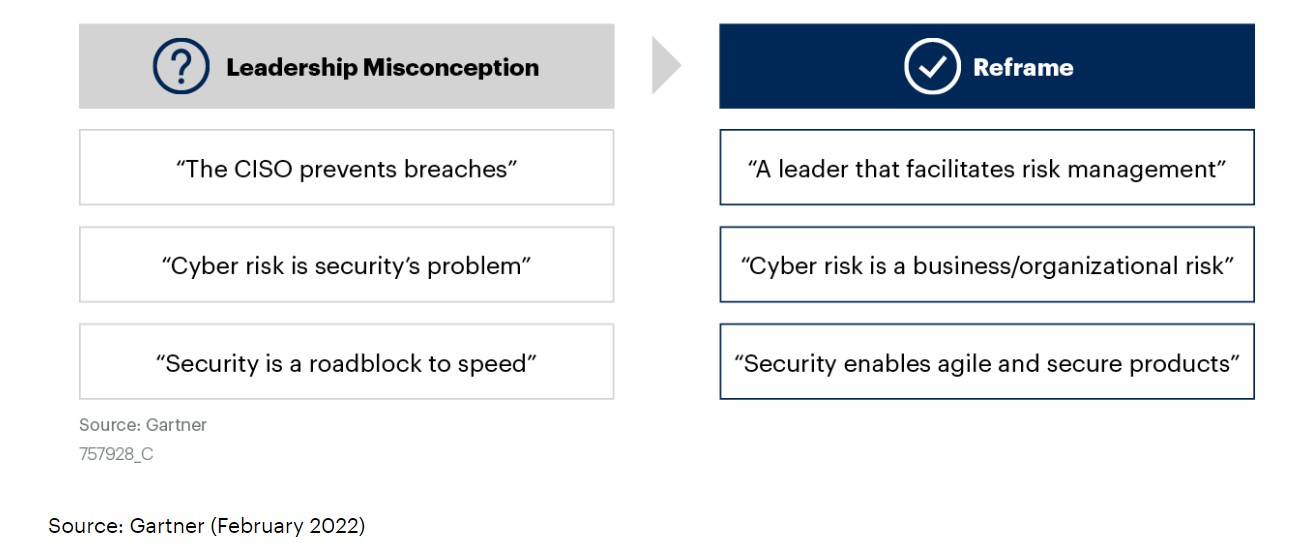
According to a study by Gartner 80% of security and risk management leaders (SRM) consider cybersecurity as a business risk rather than just a technical IT problem. The same study also implies that by the end of the year 2026, 50% of C-level executives will prioritize performance requirements based on cybersecurity risk assessments on their employee contracts.
Moving towards cloud IAM will enable cybersecurity leaders to have more flexibility in allowing people in several roles within the organization to participate in the strengthening of the organizational cyber-defense mechanism. The cybersecurity leaders will be able to decentralize and have less direct control over many impending cybersecurity decisions which will prove to be a better strategy for organizations. This will help transcend the “accountability for cyber risks and its mitigation beyond IT,” which according to Gartner is the need of the hour.
As you may have guessed, this can be done in many different ways depending on what your needs are as an organization. For example, if you have a web application running on AWS S3 buckets then you could use IAM policies to specify how the buckets should be accessed by end users (e.g., read-only or read/write). This would allow you to control who has access to which bucket using attributes like “Read Only” or “Modify Objects” which would limit who can modify files within those buckets as well as prevent them from deleting files altogether unless explicitly authorized by someone else involved with management policies.
Conclusion
Cloud IAM has a lot of potentials and can be used in many different ways. By leveraging a cloud-based IAM maturity model one can better understand how his company is performing in an IAM capacity. It’s also a useful tool for determining where one needs to focus his attention, and what types of improvements one may be able to make.
There are a few things to consider before moving to a cloud-based IAM service.
First, consider the size of your organization. If you’re a small company with less than 10 employees, it may be more cost-effective to use a local IAM service instead of going through the hassle of setting up an account with a cloud-based service. This is especially true if you have only one or two users who need access to their own accounts.
Second, consider where your data is stored—especially if it’s offsite and in the cloud. You’ll want to make sure that the data you need can be accessed easily and securely from any location, which means having redundancy in storage locations if possible. If not, try to find an inexpensive solution that will help ensure your data security while minimizing costs by minimizing the storage space needed for backups or transfers between locations (which may require extra bandwidth).
Third, think about how much time each user spends on their account each day. If they spend a lot of time working on it every day, then they might benefit from having all their data stored on-site so they can work offline as much as possible without worrying about losing access to their work.
In general, asking yourself the following questions might help in deciding whether a cloud IAM service would be apt for you:
– How much control do you need over your users’ access?
– How much data do you have to manage?
– How much of your data is stored in other countries?
– What happens if your business shuts down or goes out of business?
Cloud IAM (Identity and Access Management) is the process of determining who can access applications and infrastructure, managing users, entities, permissions, and roles in a secure manner. The Global Information Security Workforce Report 2018 reveals that the number of skilled workers for cloud identity management is expected to grow over three times as fast as it has over the last 10 years.
By using the cloud IAM model, enterprises can ensure that they are fully equipped to handle today’s complex data challenges.

